When teams start thinking about user access, it’s natural to reach for one provider that “does it all.” Many authentication vendors now offer something that looks like authorization: assign roles, toggle permissions, gate access to routes. It seems easier: one SDK, one dashboard, on bill. But bundling the two systems hides a long-term architectural cost.
Authentication and Authorization Solve Different Problems
Authentication answers: who are you?
Authorization answers: what can you do?
They may sound related (and they are), but they operate on completely different layers of your system. Authentication establishes identity; authorization evaluates permissions, relationships, resource context, and data to decide whether an authenticated actor may perform an action.
Example: authentication proves hazal@company.com is Hazal.
Authorization determines whether Hazal can edit the project open-source-docs, view billing reports, or deploy to production—based on org membership, project role, and environment constraints, not just identity.
Stretching the authentication layer to enforce business rules works only in simple systems. As complexity grows, the model stops scaling.
Why Identity Providers Aren’t Designed for Authorization
Identity Providers (IdPs) exist to implement authentication standards: SAML, OIDC, and LDAP. Their value proposition is conformance: reliably verifying identities across organizations, devices, and protocols. Because authentication is standardized, organizations can adopt consistent workflows and semantics without much customization.
Authorization has the opposite shape. Instead of following a protocol, it expresses application-specific business logic: who can perform which action on which resource under which conditions. Every product models its domain differently, and authorization systems must adapt to those models. Their value lies in flexibility, not standardization.
Expecting one product to excel at both is unrealistic. Authentication is about interoperability; authorization is about representing and evolving business rules. Extending IdPs into authorization pushes resource semantics into identity constructs that were not designed to capture fine-grained relationships.
The same pattern shows up outside security as well. ClassPass recently added a “Food and Drink” workflow to an application designed for booking fitness classes.
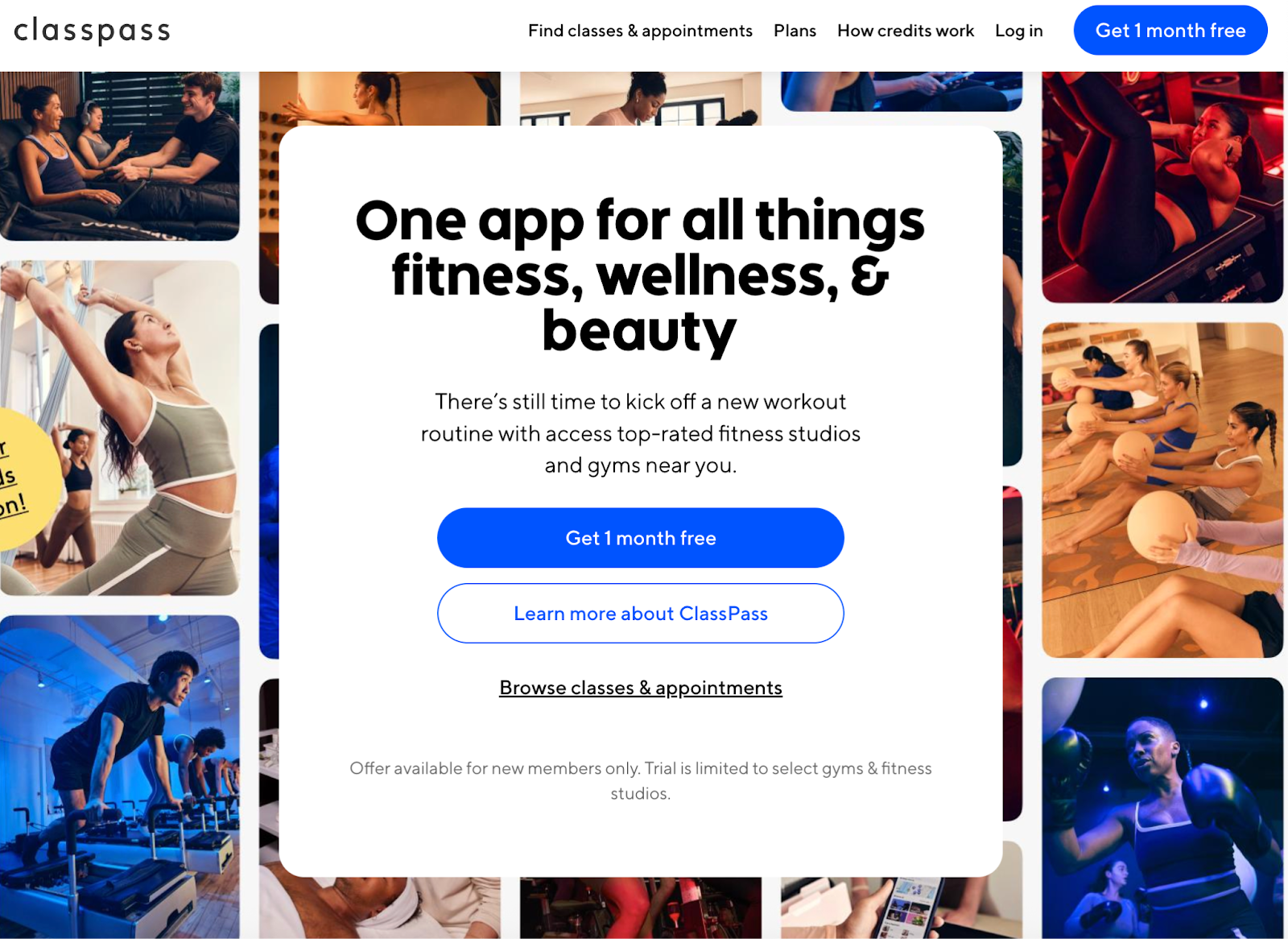
The interface still uses visit-based language (“25% off your first visit”) because the underlying system was built for gym reservations, not food ordering. The product works, but the mismatch is visible.

Similarly, IdPs such as Okta, Google, or Active Directory are great at identity workflows but not at evaluating permissions across an application’s resource graph. The architectural seams appear for the same reason: using a system outside its intended domain.
When Authentication Platforms Try to Add Authorization
A common question from engineering teams is whether an authentication platform can eventually become the system of record for authorization. On the surface, centralizing identity, onboarding, billing, and access control into one provider feels simpler. But the technical boundaries that separate authentication from authorization show up immediately once applications require fine-grained access control.
Authentication systems can attach coarse identity metadata (such as which tenant a user belongs to or a high-level role) but these attributes do not capture the relationships, resource structures, and contextual data that real authorization depends on. As systems evolve, permissions often need to reflect resource ownership, workflow state, environment constraints, or user-resource relationships. These cannot be represented cleanly through identity constructs alone.
This tension has appeared repeatedly across the industry. Several identity platforms have experimented with two parallel authorization approaches:
- A simple role or group model embedded in identity tokens, suitable only for coarse, static permissions and subject to issues around staleness and revocation.
- A separate fine-grained authorization service, backed by its own data model and decision engine, because resource-level permissions require storing and evaluating information that does not live in the identity layer.
The existence of two unrelated mechanisms inside the same platform underscores the underlying architectural distinction: authentication and authorization serve different purposes and rely on different data. In many cases, these fine-grained authorization products were later discontinued, reflecting the difficulty of reconciling the two problem spaces within a single system.
Teams evaluating these approaches often reach the same conclusion: authentication providers excel at identity workflows, but they are not designed to represent or evaluate access over an application’s resource graph. Fine-grained authorization requires its own model, lifecycle, and operational boundaries.
Challenges of Using AuthN for Authz
Static Groups vs. Dynamic Authorization
IdPs expose authorization primarily through coarse grained attributes like users, groups, and roles. This works when the set of protected resources is small and stable. It breaks down in systems where applications create resources dynamically. For example: datasets, pipelines, or model versions per tenant or workflow.
Because IdPs have no insight into the application’s resource graph, teams often approximate authorization by creating groups per project, per environment, or per dataset. Over time this leads to thousands of groups, unclear naming conventions, and brittle mappings that drift from the actual access semantics.
Dynamic authorization evaluates access based on real-time facts about users and resources, often sourced from application data. This makes it more suitable for representing fine-grained, contextual permissions as the system evolves.
Limited Visibility and Auditing
IdPs record authentication and group membership but cannot show the effective permissions derived from that membership. They cannot answer:
- Which resources can this user access right now?
- Who granted that access and when?
- Under what conditions does it expire or escalate?
Audits then require manual correlation across systems. During compliance reviews (e.g., SOC 2, ISO 27001), teams often reconstruct mappings from logs or exported data, increasing effort and uncertainty.
Authorization systems log access decisions explicitly, making it possible to reason about why a permission was granted.
Built for Users and Groups, Not Permissions and Resources
IdPs manage identities (users, credentials, groups), not application resources. Their model assumes group membership implies access, which only supports coarse-grained authorization.
Real applications require contextual access: users may own specific resources, collaborate on others, or interact with only subsets of objects. Implementing this with groups leads to role explosion and unmaintainable taxonomies.
IdPs cannot express rules like:
- “Users can edit documents they own.”
- “Contractors can view customer data only during active projects.”
These require evaluating real-time attributes or relationships that live inside the application domain.
The issue isn’t fragility, but a mismatch of responsibility. IdPs handle identity. Authorization logic belongs closer to the application and its data model.
Benefits of Decoupling AuthZ from AuthN
Multiple Protocols, One Policy Layer
Most systems support multiple authentication mechanisms simultaneously (SAML for enterprise SSO and OAuth for public APIs). Coupling authorization to any one protocol creates duplication and inconsistency. A separate authorization layer allows identity mechanisms to change without modifying access rules.
Simpler Migrations and Maintenance
Identity systems change over time: companies switch providers, consolidate directories, or reissue credentials. When authorization depends on identity provider data, these transitions become risky and complex. Decoupling ensures identity changes do not alter permissions.
Testability and Isolation
Independent authorization logic can be tested without authenticating real accounts. Engineers can evaluate policies deterministically and isolate regressions.
Domain Separation
Large products often model user relationships differently across domains (billing, content, analytics). These systems should share a stable identifier but evaluate permissions locally. Clear boundaries improve maintainability and resilience.
Organizations such as Tamr followed this path: after modernizing authentication with Auth0, they replaced Keycloak with an authorization system suited for expressive, scalable policies. By adopting Oso, they centralized authorization logic and improved maintainability.
Let’s Decouple Them: How Authorization as a Service Works
A smart approach to implementing this separation is Authorization as a Service (AaaS) where access control is isolated in its own layer. Applications send queries, often in the form can(user, action, resource), to evaluate whether an operation should proceed. The service checks a policy and the relevant user or resource data, then returns an allow/deny decision.
Advantages of this model include:
- Decoupled policy management: Policies can be updated or reviewed independently of application code.
- Isolated testing: Rules can be validated without deploying or modifying the application.
- Layered performance optimization: Authorization results can be cached within the authorization layer, reducing latency and external calls.
This preserves flexibility in authentication while centralizing authorization logic in a domain-appropriate system.
Conclusion
Authentication solves the who problem.
Authorization solves the what problem.
Authentication happens once per session; authorization runs on the critical path of every request.
Blending the two introduces unnecessary coupling. As identity systems evolve, authorization should remain stable and defined by your application’s data and policies. Clear separation (especially via an AaaS model) ensures access control remains correct as systems grow in complexity.
Want to talk through how this separation could work in your system? Meet with one of our engineers; we’ll walk you through modeling authZ independently from your IdP.