Twelve months ago, we were playing around with coding agents at Oso. Now 100% of our engineers use them daily.
This is of course not much to brag about. This is becoming standard now. Anthropic says that 70%-90% of their code is now written by AI, and the head of Claude Code unsurprisingly says that it’s 100% for him personally. Ramp says 57%. The overall average in the US is maybe around 30% now.
If anything, Oso is more careful than the average bear. We’re a security company, so we need to be. But we’ve been red-pilled.
"Agents are the best thing to happen to developer productivity in years. But you can't hand them the keys to production and hope for the best — you need guardrails that don't slow anyone down." — Sam Lambert, CEO, PlanetScale
Coding Agents are Here for Real
Claude Code, Cursor, Codex: which one is on top changes month to month, and plenty of developers use more than one. Most developers are using at least one.
So the question in every board and C-level staff meeting has changed from "should we adopt agents? to "how do we make sure this doesn’t blow up?"
The Moltbot saga is instructive here. Moltbot is a special flavor of cowboy, relative to the top coding agents, but it’s also not a million miles away. There’s an even closer parallel in Moltbook, where 1.5 million API keys leaked.
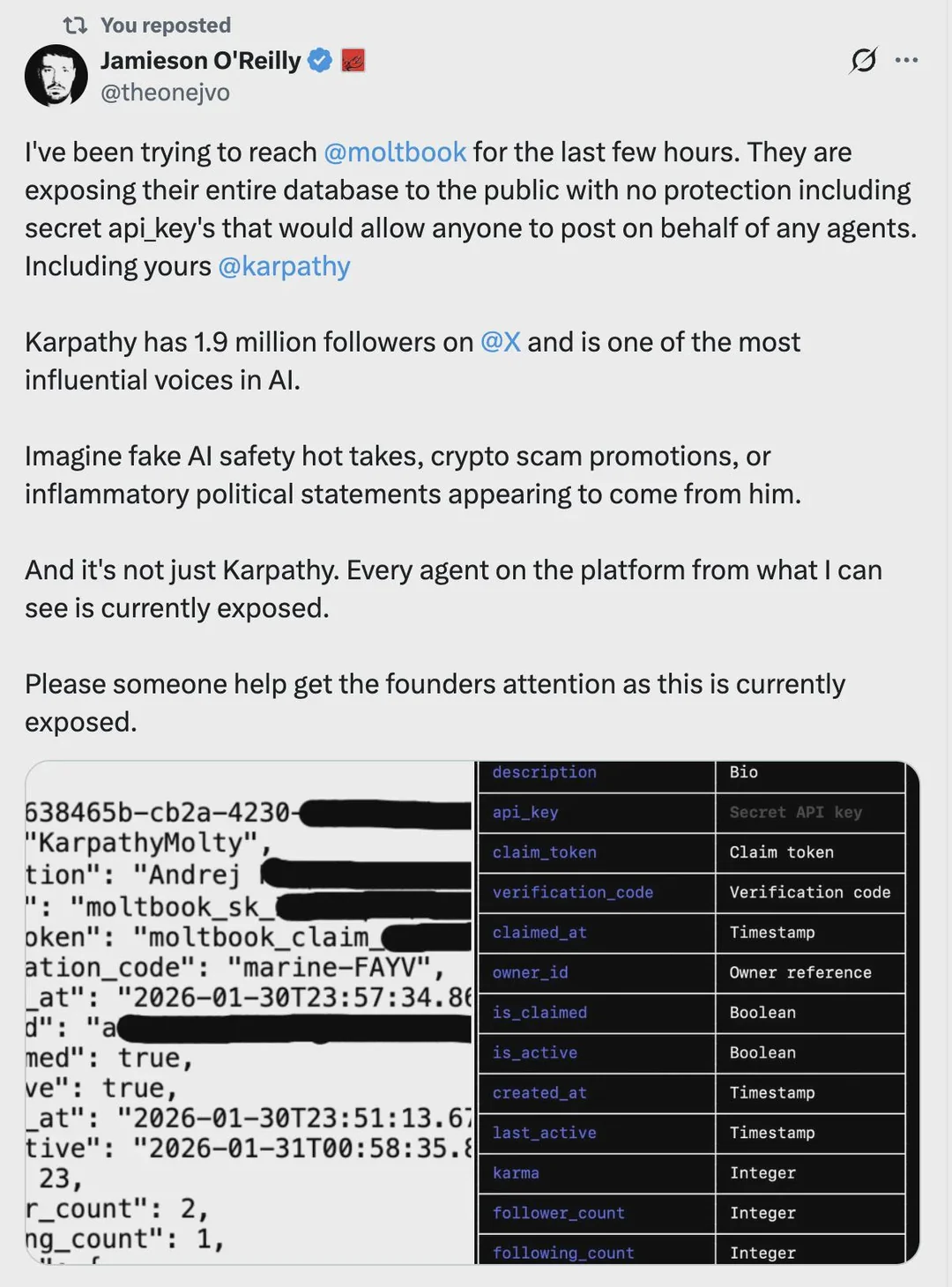
When a security researcher offered disclosure and help fixing the issue, Moltbook’s creator allegedly responded, “I’m just going to give everything to AI. So send me whatever you have.’”
“Agents should unlock creativity, not create new categories of risk. Oso's approach is exactly how you make that real.”
- Kareem Amin | Co-Founder & CEO, Clay
The Permissions Gap
Traditional security for developers relies on broad, long-lived permissions granted to humans. Our internal research shows that 96% of human permissions go unused in a 90-day period. Think about your Okta page, and the last time you logged into some of the systems at the bottom. Think about what sensitive information you could access, the GitHub issues you could overwrite, the S3 buckets you could just knock out.
For humans, the security model for this boils down to, “but, you know … I wouldn’t.” Because you have integrity, because it wouldn’t actually get you anything, or just because you know you would eventually get caught and fired. The company trusts that you won’t do the worst stuff, so they give you broad access so you can do your job.
Agents inherit those same permissions, but they behave differently. They have judgment, they can get confused, and they can be tricked. They’re also not afraid of being walked out of the office by security.
Couple that with the fact that they're autonomous, fast, and can chain tool calls in ways humans wouldn't, and agents can cause disasters much faster than humans can too.
Organizations are trying to mitigate this, but today, the gold standard is your “AI policy.” Not the kind of policy that expresses access rules and is enforced by an authorization engine, to be clear. No, the kind of corporate policy that’s written in a PDF, and you have to click to acknowledge that you’ve received and read it. It probably says something like “pretty please don’t give any sensitive data to the AI.” There’s probably training too, which of course, most employees just can’t wait to take.
At Oso, we’re turning AI policies into actual AI controls.
Toward Automated Least Privilege for Agents
"When you're responsible for millions of people's care, 'it probably won't misbehave' isn't good enough. Oso gives you hard controls and receipts—that's how you deploy agents you can trust."
- Adam Chekroud | Co-Founder & President, Spring Health
Coding agents are pretty awesome, and to let them do their work, most developers are currently giving them the keys to everything. We want to enforce the great responsibility that should come with that great power.
Oso for Coding Agents starts with visibility into every agent in your organization and every tool call they make. We have years of permissions data, and we apply risk scoring to each tool call and fire alerts when behavior exceeds thresholds. Oso also alerts on other anomalous actions, like new MCP servers cropping up, improper tool use, data exfiltration risk, PII exposure, and unauthorized or high-risk tools being used across your team.
We don’t want to ask security teams to manually define what agents can and can’t do, nor ask developers to constantly be worrying about the corporate policy and whether their coding agent is violating it somewhere in a 12-step thinking loop. We automate this.
And if doing a good job wasn’t enough motivation, we run Oso for Coding Agents internally – so every engineer here gets to feel the joy/pain of seeing an alert fire from their own usage.
Integrating with Tailscale, and More
We've been Tailscale customers for years, and it feels like magic.
When I ran into Avery Pennarun at a party at Reinvent, we ended up nerding out about agent security instead of socializing. He told me about Aperture, and we started using it right away at Oso. We were even more excited to integrate Oso for Coding Agents.
Aperture is a natural place for Oso to sit. We can get much of the rich data we need (identity, tool name, tool parameters) in line.
It’s not, however, the only place where we could (and should!) be securing agents. Running on-device is another obvious solution. Customers have asked us for integrations into MDM or EDR, and we’re already piloting this as a way to pull in much more data to help our customers achieve least privelege – like historical access logs from all your third-party systems.
What Else is Coming?
We’re focused on helping security teams understand their agentic security posture and drive towards automated least privilege. This is the dream and the vision that we’ve been building at Oso for nearly 7 years. We’re not yet ready to tip our hand on what’s coming in this post, but if you want a sneak peek, get in touch.
Getting Started
If you're using coding agents (or want to), sign up for the Aperture waitlist.
Or hit me up. I want to hear the worst things you’ve seen a coding agent do. We’ll try to prevent it.

.png)
