Coding agents are everywhere. See what yours are doing.
Articles about authorization, and other news from Oso's engineering team

Find out the hidden complexities of CRM authorization and learn how to do recursive authorization with Oso

Master resource-specific roles with Oso. Learn scalable permissions like Google Docs, GitHub, and Figma using Polar examples for flexible authorization.

Evan Ziebart, Software Engineer at Duolingo, takes us through their journey from a home-grown solution to moving to Oso and hugely simplifying their process for managing user permissions.

How Oso provides EMR apps with the flexibility they need

The updates to Oso’s Local Authorization in the V2 SDKs make it easier to build flexible authorization workflows.

Fallback ensures your app remains up and operational, even in the case of an unexpected Oso Cloud outage.
We just led a webinar on How Google handles Authorization at scale, watch to learn more about whether it is the best approach to secure your application permissions
.avif)
ReBAC - especially Google Zanzibar's implementation of it - is the wrong abstraction for authorization.

Simplified fact management and powerful query builder API's - and much more!
.avif)
Simplified fact management and powerful query builder API's - and much more!

A look into the pros and cons of using TypeScript versus JavaScript, plus some thoughts on why there is so much drama around them lately.

A new set of reference material to help users take Oso into prod

Ashwyn Nair, Senior Software Engineer at Sensat, dives into how Oso has helped them create a safe space for their users to have full control over who can access their data.
.avif)
Generate TypeScript types from your Polar policy - and much more!

Polar now has its own language server implementation, making it easier to write your authentication policies

Peadar Coyle, Founder at AudioStack, dives into how they went from a homegrown authorization framework to using Oso and why it was critical to make this change for a GenAi company where protecting data is mission critical.

Why we moved from Fargate to ECS on EC2, and how we preserved a zero-downtime architecture in the process.

Announcing a new feature in authorization policies: a limited form of negation (not syntax).
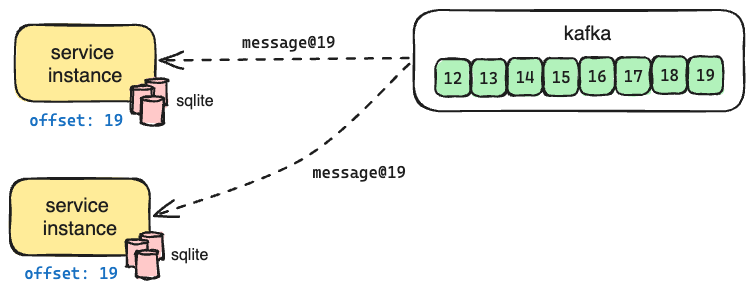
How Oso uses Kafka and an Event Sourcing Architecture to deploy a highly-available, low-latency managed authorization service.

Adding access control to LLM chatbot responses with Oso Cloud and Postgresql

A comprehensive look at the design of Polar, and how we enabled it to operate over distributed data.
.png)
Using local data to answer authorization questions with Oso Cloud

A sample app that demonstrates RBAC, ReBAC, and ABAC in Node.js with Oso Cloud

This post provides specifics on when to use Oso, and when not to.