Coding agents are everywhere. See what yours are doing.
Articles about authorization, and other news from Oso's engineering team

Learn how to secure your RAG pipelines using Oso’s new SQLAlchemy integration. Apply fine-grained authorization directly to your database queries—including those using pgvector—without writing custom SQL. Prevent data leaks in LLM apps, simplify permissions, and build safer AI features with Python and SQLAlchemy.

As AI apps like RAG chatbots integrate with Google Drive, Notion, and Jira, one challenge dominates: preventing data leaks. This post explores three architectural approaches to secure AI access with real-world tradeoffs and guidance from Oso engineers.

Learn how we built a step-by-step debugger for Polar, our Datalog-inspired logic language for fine-grained authorization. This post explores coinductive trees, lazy evaluation, and why a TUI made more sense than a GUI for tracing recursive, rule-based decisions.

Introducing Oso Migrate: A TUI that simplifies authorization migrations.

Authorization seems simple until you build it. Learn from 40 common mistakes developers make when tackling one of the toughest problems in software.
.png)
Tido Carriero shares career advice for engineers, his 3-pillar framework for fulfillment, and why Oso’s approach to authorization inspired him to become an advisor.
.png)
A wake-up call for SaaS: JPMorgan exposes deep security flaws. See how top vendors are rethinking authorization with Oso to win enterprise trust.
.png)
A weak password exposed full admin access and sensitive customer data. Learn from this real-world breach before it becomes your own nightmare.
.png)
Oso Self-Hosted is now in private beta! Run Oso in your AWS account for full control over authorization infrastructure, data, and compliance.

Is your app's authorization logic holding you back or putting you at risk? Discover 5 critical signs your permissions system is fragile—and how to fix it before it breaks. Learn from real-world examples and best practices from Oso,

Learn why sub-10ms authorization is the new gold standard for enterprise apps. Discover how Oso delivers lightning-fast, scalable permission checks without compromising on flexibility or control.
.png)
Discover "A Tour of Polar," Oso’s interactive, point-and-click guide to building authorization policies. Learn RBAC, ReBAC, and ABAC with editable policies and real-time authorization decisions in a fun, hands-on experience.

Learn how to simplify and scale your authorization tests in Oso Cloud using assert variables and the iff operator. Write fewer test cases, validate multiple permissions at once, and ensure your access control policies stay correct as they grow.

Learn how Oso Cloud enables fine-grained access control in microservices using RBAC, ReBAC, ABAC, and Polar—our purpose-built policy language.

Oso Sync ensures your authorization data stays consistent between your app and Oso Cloud by detecting and fixing data drift caused by issues like latency or manual changes. It supports PostgreSQL, MongoDB, and CSVs for other databases, offering both reporting and automatic updates.

Discover how Sensat transformed its authorization system with Oso! Learn how they built fine-grained access control, implemented permission inheritance, and eliminated API code changes—all while streamlining development. Read more!
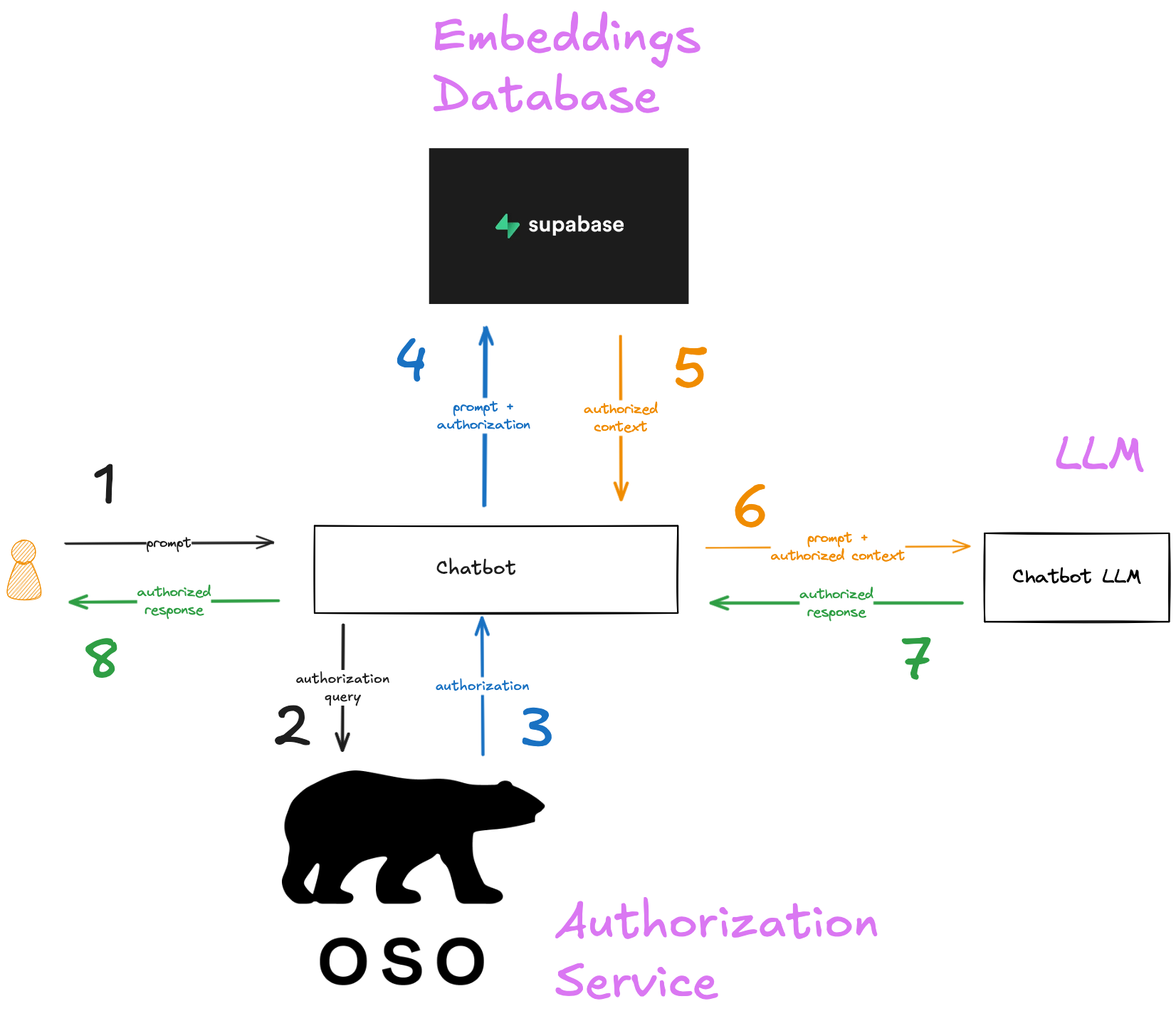
Use Oso Cloud, OpenAI, and Supabase to build a permissions-aware RAG chatbot, so users only see context from documents they have permission to view.

Join our upcoming O’Reilly SuperStream: Retrieval-Augmented Generation (RAG) in Production.

Duolingo migrated to Oso to simplify authorization and improve developer productivity. Previously, permission changes took hours or even days—now, they take minutes. In this interview, Tom Whittaker, Senior Engineering Manager at Duolingo, shares how Oso helped them focus on core business features instead of workarounds. Watch the full story and explore real-world authorization insights from top engineering teams.
%202.png)
List filtering is the process of retrieving only the data a user is authorized to access, rather than fetching everything and filtering in-memory. In an LLM chatbot, this means ensuring users only see responses or documents they have permission for. Instead of checking authorization for each item one by one, which is slow at scale, Oso Cloud provides two efficient methods: centralized filtering, where the chatbot queries Oso Cloud for a list of authorized item IDs before retrieving them from the database, and local filtering, where Oso Cloud generates a database filter to apply directly in SQL, reducing unnecessary data transfers.

Accordingly, vector databases were positioned to be the next it category of data storage—following previous waves that targeted search (e.g. Elastic), unstructured data (e.g. MongoDB), and analytical data (e.g. ClickHouse). Today, however, it’s unclear if vector databases will remain a standalone category. A vector database is more of a conduit for language models—the models do the heavy-lifting, handling vectorizations (i.e. creating embeddings) and re-ranking. Accordingly, the database depends on these models to carry-out vector search. This raises the question: are vector databases actually an independent category, or is vector search just a need-to-have feature of today’s databases?

Oso’s team offsite at Hemlock Neversink was all about bonding, strategy, and fun—goat hikes, team workshops, and even casino lessons in access control. We returned recharged, motivated, and stronger than ever. Want to join us next time? We’re hiring!

List filtering is the process of retrieving only the data a user is authorized to access, rather than fetching everything and filtering in-memory. In an LLM chatbot, this means ensuring users only see responses or documents they have permission for. Instead of checking authorization for each item one by one, which is slow at scale, Oso Cloud provides two efficient methods: centralized filtering, where the chatbot queries Oso Cloud for a list of authorized item IDs before retrieving them from the database, and local filtering, where Oso Cloud generates a database filter to apply directly in SQL, reducing unnecessary data transfers.

We just led a webinar on Fine-Grained Authorization in Python, watch to learn more about whether it is the best approach to secure your application permissions.

Find out the hidden complexities of CRM authorization and learn how to do recursive authorization with Oso