How It Works
- Define authorization policies in Polar, our DSL for expressing permissions logic
- Store policies and authorization data, called facts, in Oso Cloud
- Make API calls with our client SDKs from your app when you need to answer authorization questions, like
can user X view Z resource?orwhat resources can user X edit?
Writing Policies in Polar
Oso Cloud’s policy language, Polar, is designed for expressing arbitrarily complex and granular application authorization logic. Polar can express any model, including RBAC, ReBAC, ABAC, fine-grained authorization, organizational hierarchies, and more.Data Management
Facts are a prescriptive data model for authorization-relevant data. There are multiple ways to provide facts to Oso Cloud. Which one you choose depends on your use case and application architecture.Centralized in Oso Cloud
Centralized in Oso Cloud
Data that is exclusively or extensively used for authorization, like users, roles, and permissions are best stored in Oso Cloud as facts. Oso Cloud provides a robust mechanism for synchronizing data stores and detecting drift with Oso Sync.
Stored in your local database
Stored in your local database
Oso Cloud supports centralizing your data, but doesn’t require it. [Local authorization] is our unique approach to minimizing data synchronization and data transfer. When you make a request to the Oso Cloud API, you receive back database logic that can be executed against your local data store to finish the authorization evaluation.
Provided at request time
Provided at request time
Oso Cloud also supports providing data at request time, called context facts. This is useful when you have data that is not used regularly for authorization, but is needed to evaluate the request.
Evaluating Authorization Requests
Oso Cloud can return booleans, a list of resources, a list of permissions, or even database logic that can be used to complete an authorization decision. It all depends on your application requirements.Architecture of Oso Cloud
Oso Cloud is a managed authorization service built to operate safely on the critical path of your application. Its architecture is designed to guarantee:- High availability: Authorization cannot go down when your app is up. Oso Cloud is built for continuous uptime and fault tolerance.
- Low latency: Every request may involve one or more authorization checks. Each must complete in single-digit milliseconds.
- High throughput: Authorization must scale with user activity, handling thousands of checks per second across services.
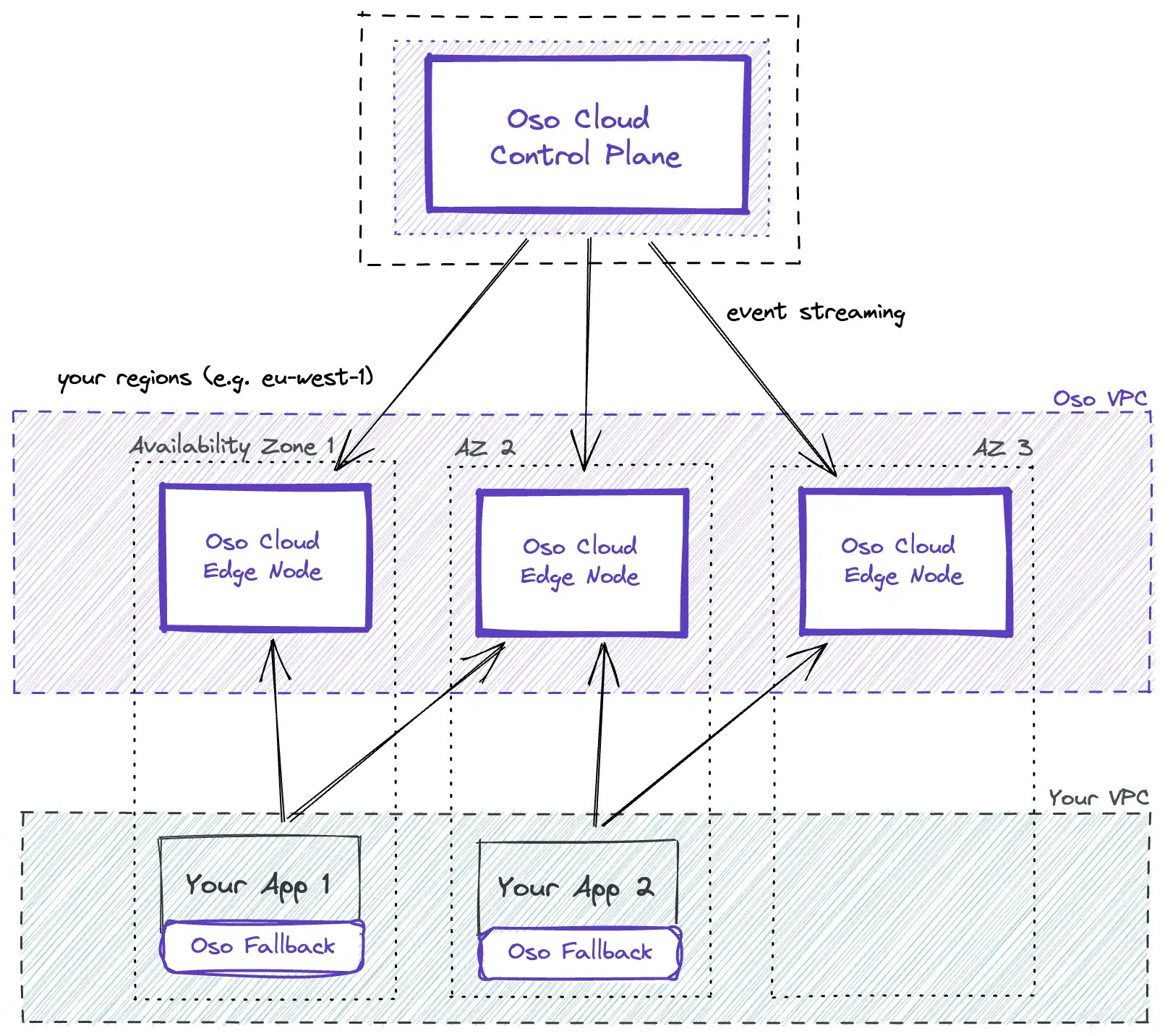
High Availability
Oso Cloud has no single point of failure. We spread Edge Nodes across regions and availability zones to protect against network failures in any particular data center and to insulate your app from any one node’s downtime, providing high availability. Oso Cloud has already withstood multiple region-wide outages without any customer-visible impact. We provide SLAs on availability. The Datadog chart below shows our measured production availability over the calendar year from Jan 30th, 2024 to Jan 29th, 2025, across many regions, 99.99% and up.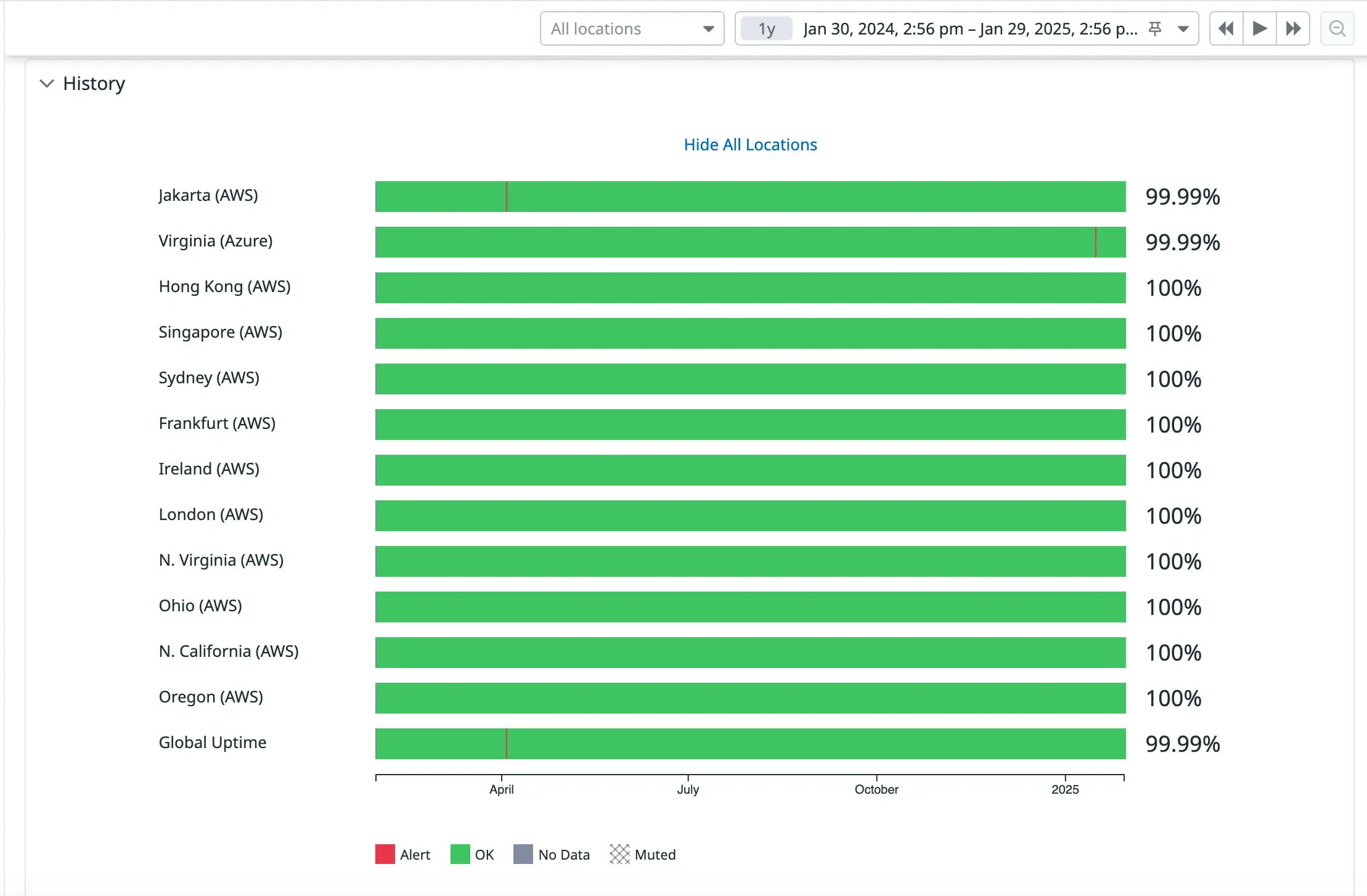
Oso Fallback Nodes
Oso Fallback Nodes
You can optionally deploy Oso Fallback Nodes colocated with your application inside your VPC. These run a current version of the Oso Cloud API and contain a copy of your rules and data to provide an extra layer of insurance you can always use to make authorization checks, even if Oso Cloud is unreachable. Fallback Nodes may lag Edge Nodes by up to 30 minutes. They are for disaster scenarios only and are not intended to be a primary server for running authorization requests.