- Create an authorization policy.
- Add user facts.
- Make your first authorization check.
What you’ll build
a basic document-sharing system where:- Alice (owner) can view and edit the budget document.
- Bob (viewer) can only view the budget document.
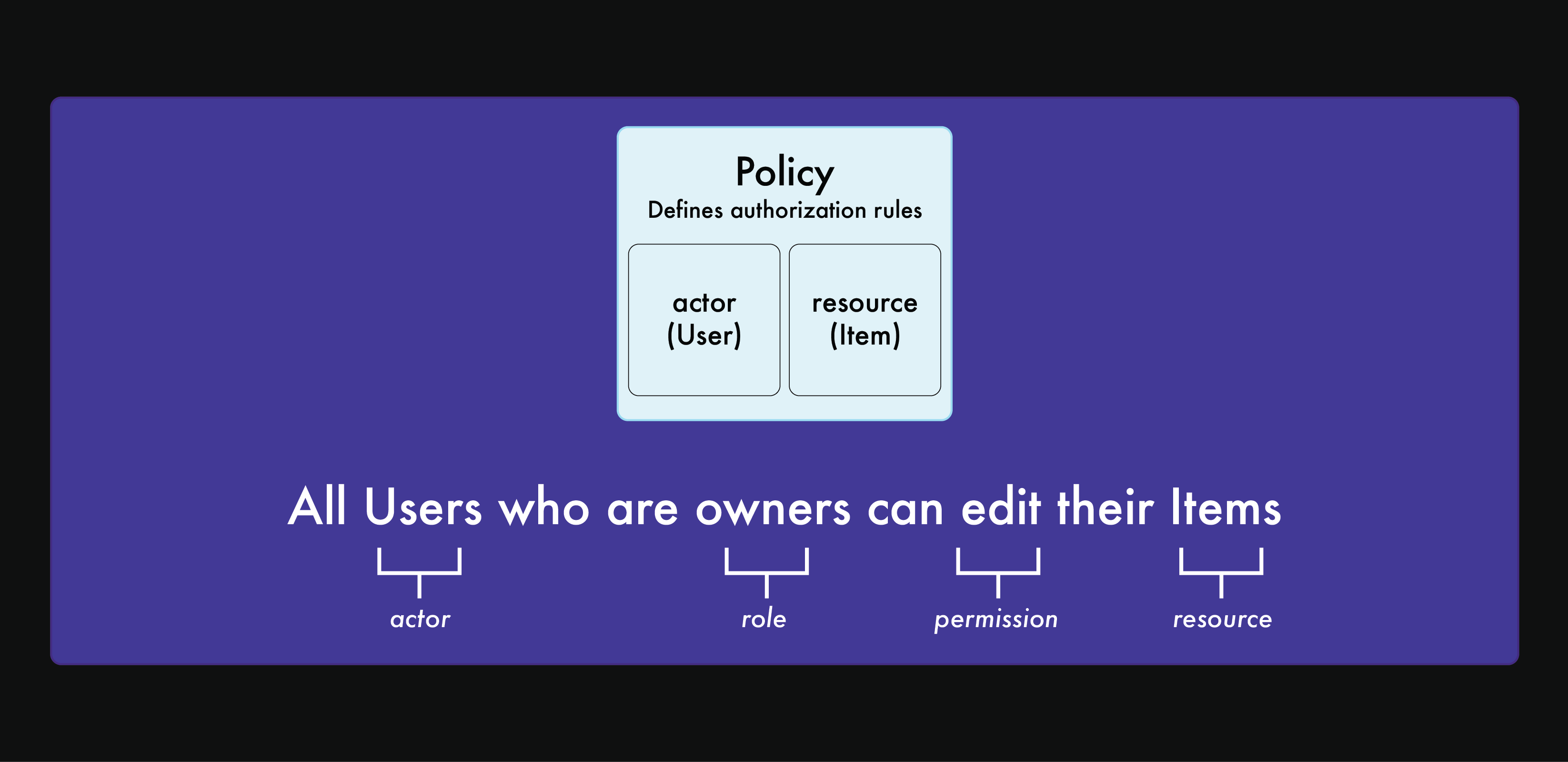
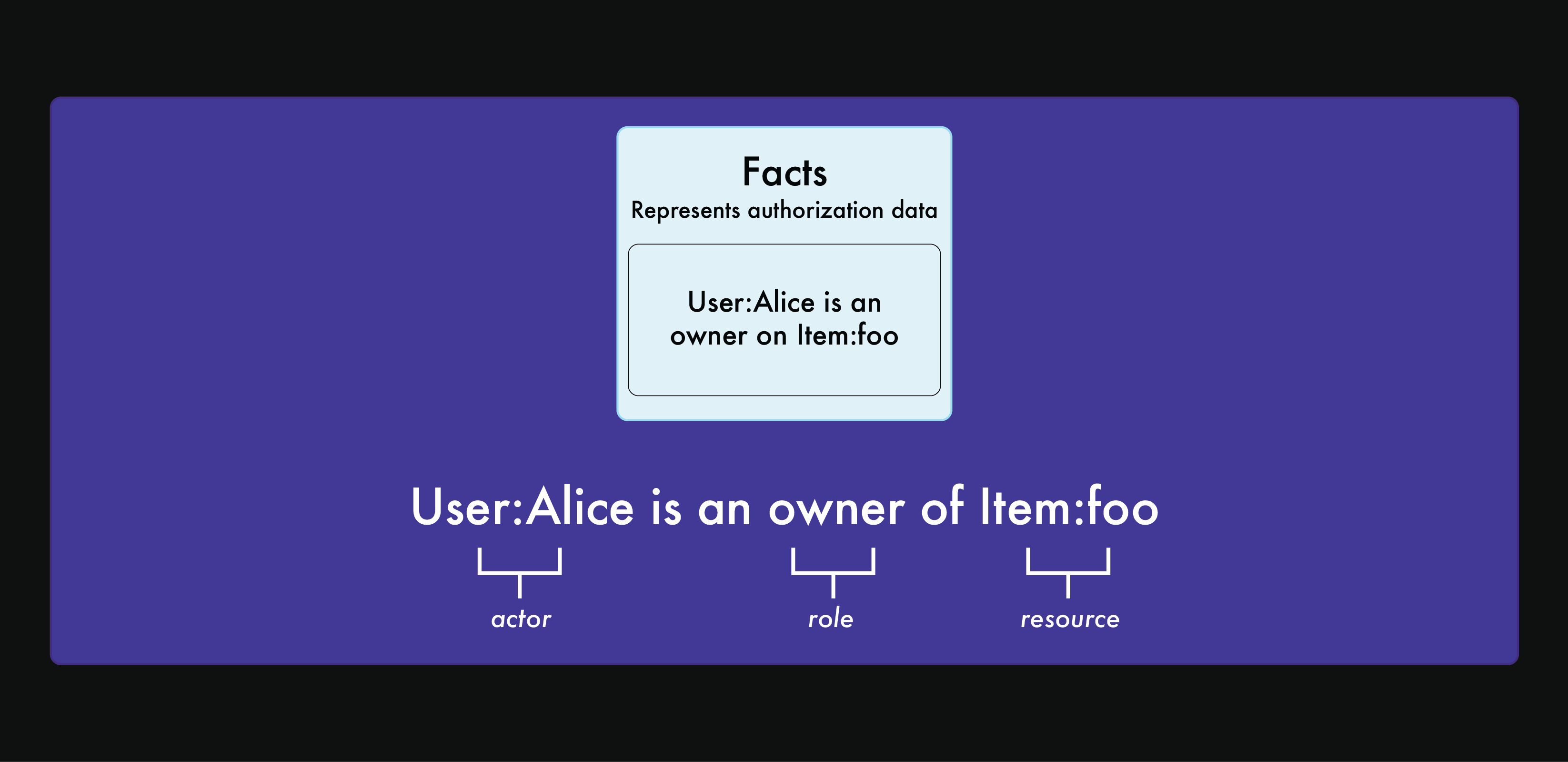
How Oso Cloud works
Oso Cloud evaluates authorization requests using two components:- Policies — Rules written in Polar defining who can do what.
- Facts — Data about your users, resources, and relationships.
Step 1: sign up for Oso Cloud
Create your free account — no credit card required. The Developer tier includes 5 developers and 100 monthly active users.Step 2: create your first policy
Open the Rules Editor and switch to Workbench mode.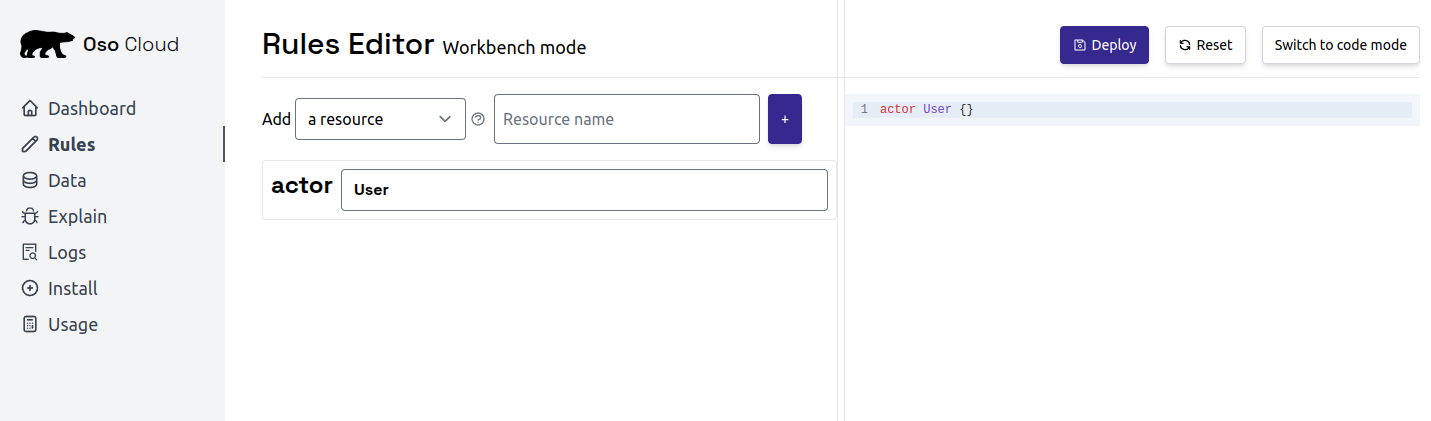
Add a resource
Create a Document resource to represent files users can access.- Click the input box next to
Add a resource - Type “Document”
- Click the
+icon
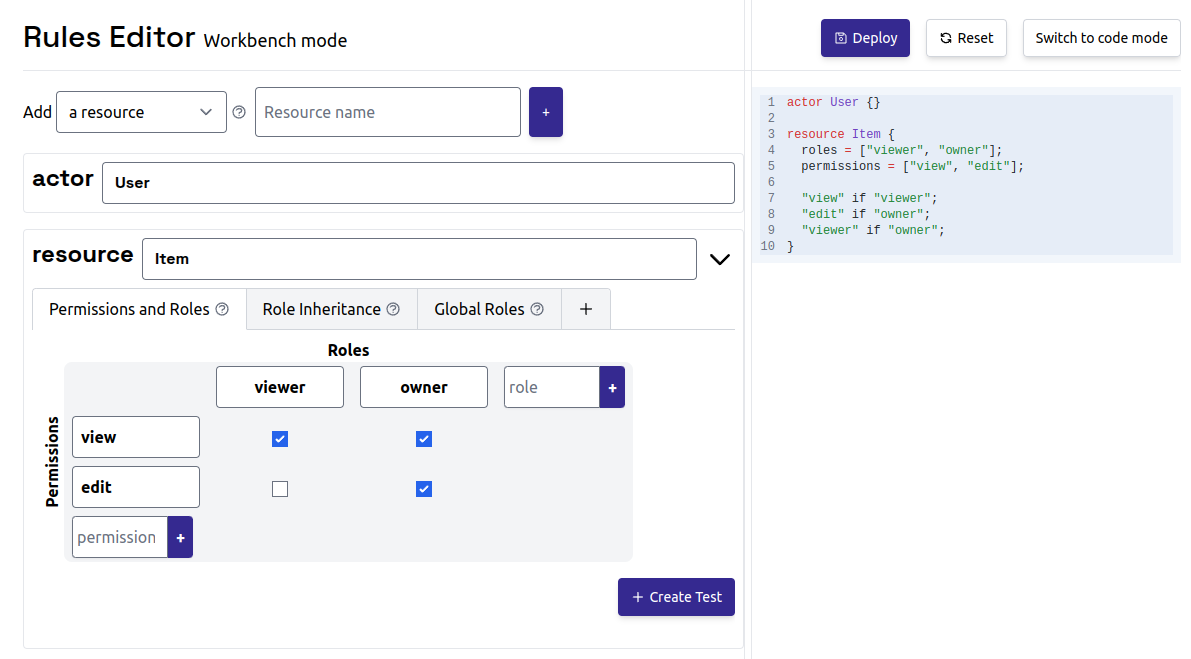
Review the generated policy
Oso Cloud generates a policy with these components: Actor:User (someone requesting access)
Resource: Document (the file being protected)
Roles: viewer and owner
Permissions by role:
viewercan view documentsownercan view and edit documents
Deploy the policy
Click Deploy in the top right to activate your policy.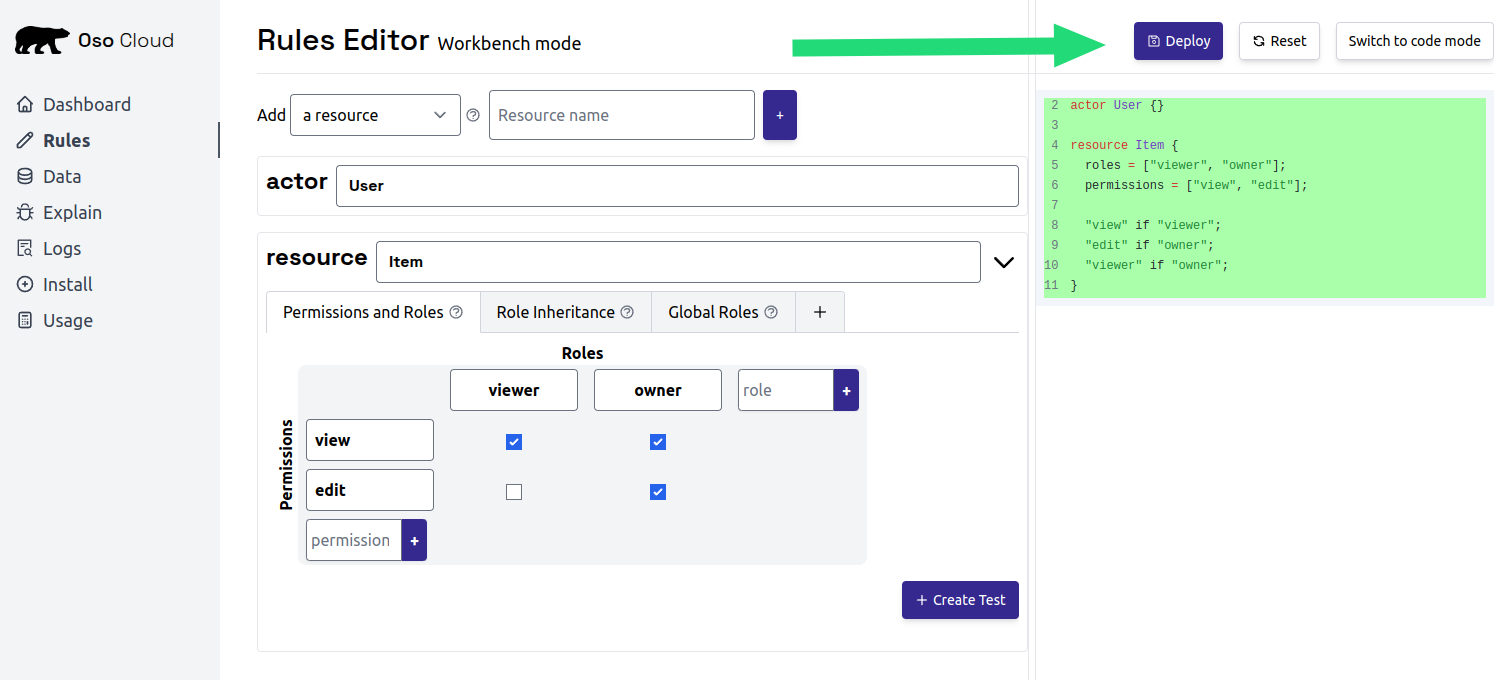
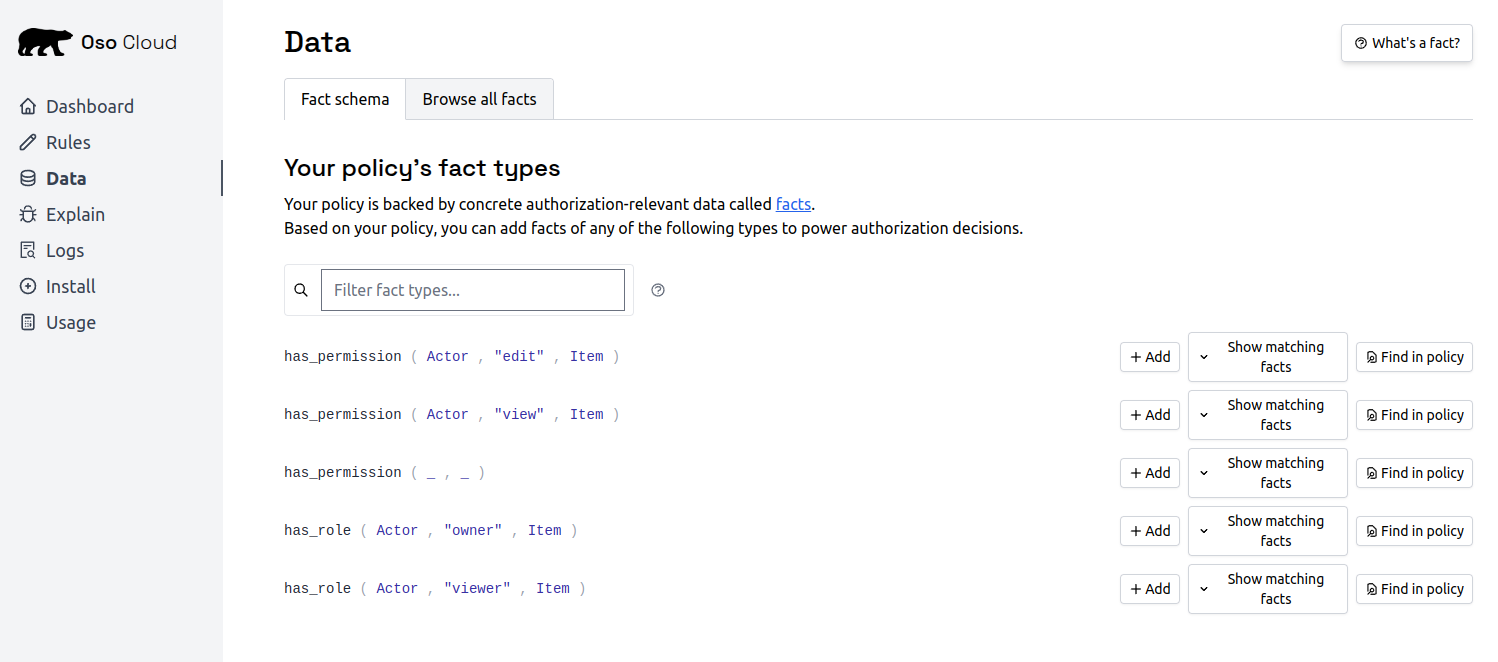
Add user and role facts
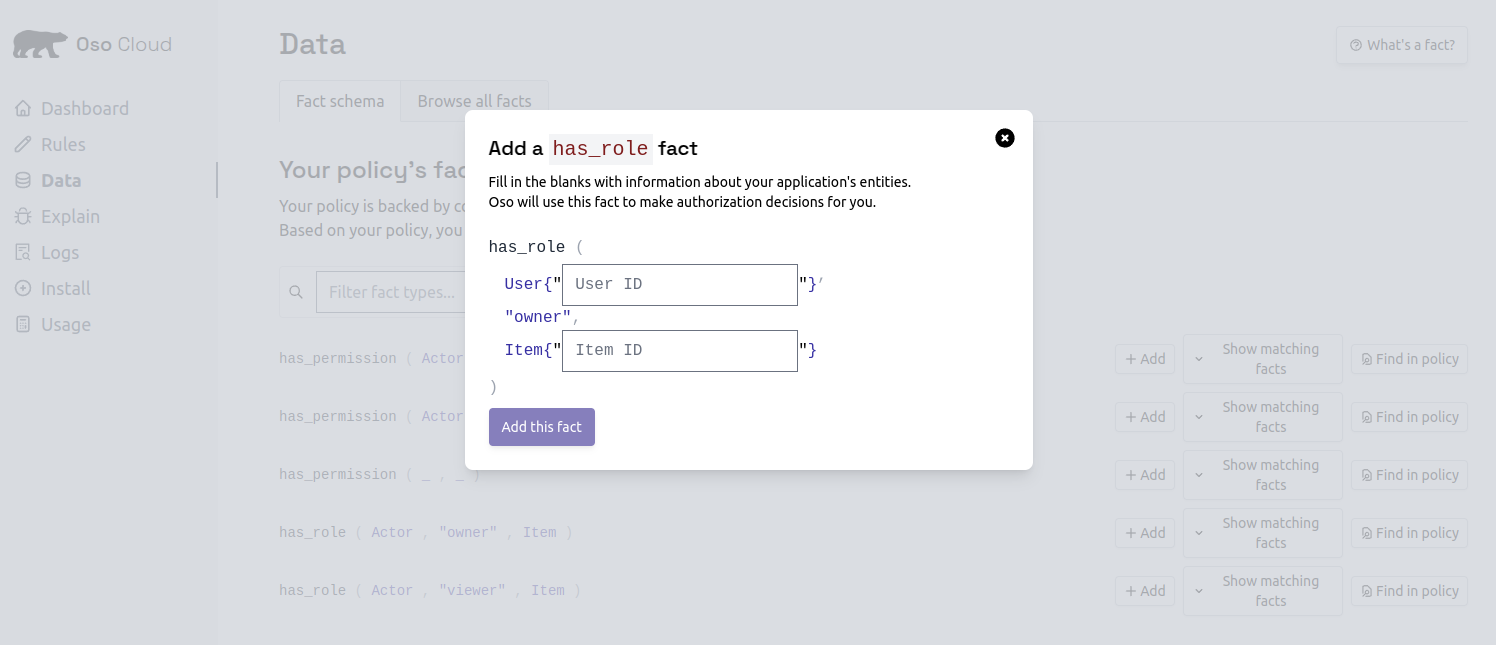
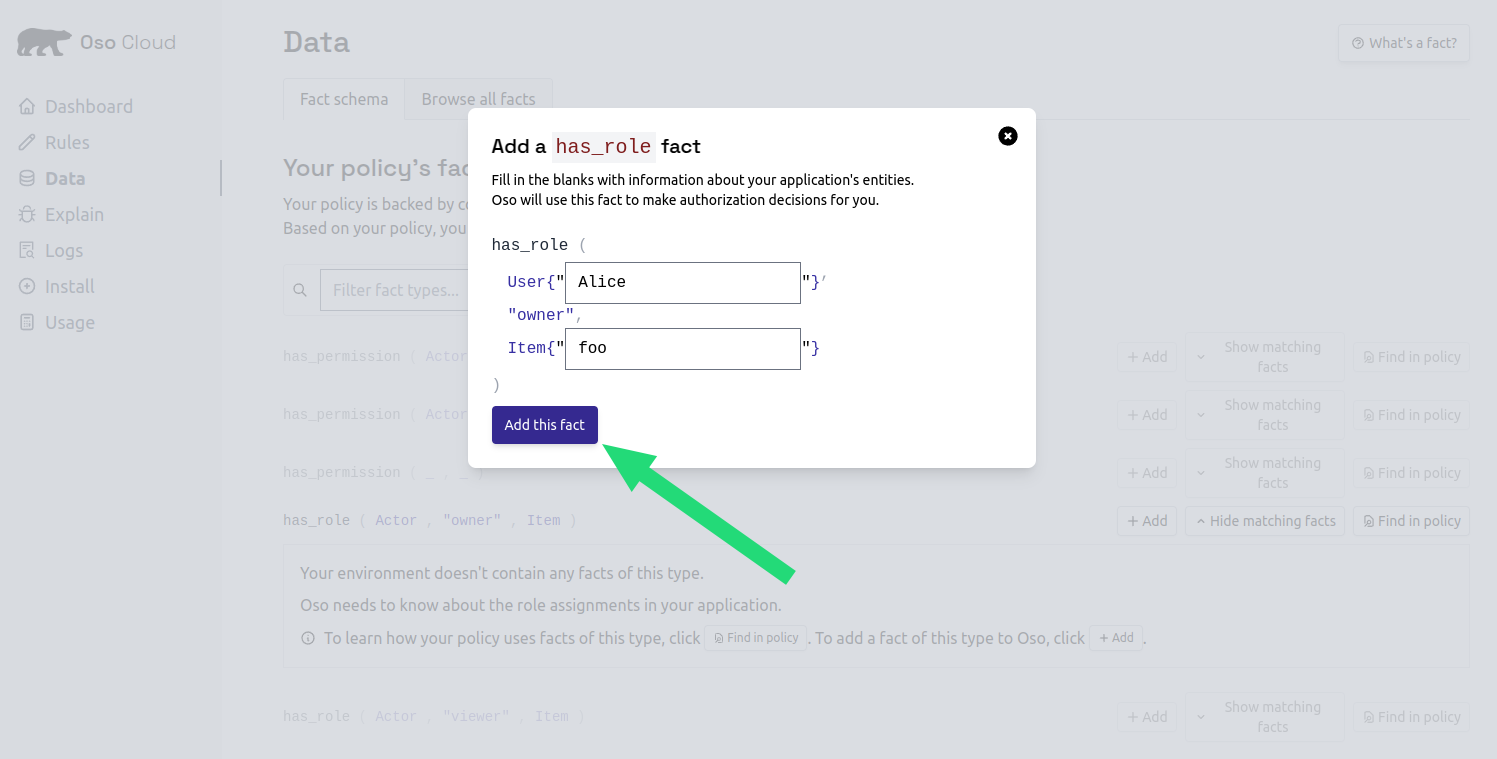
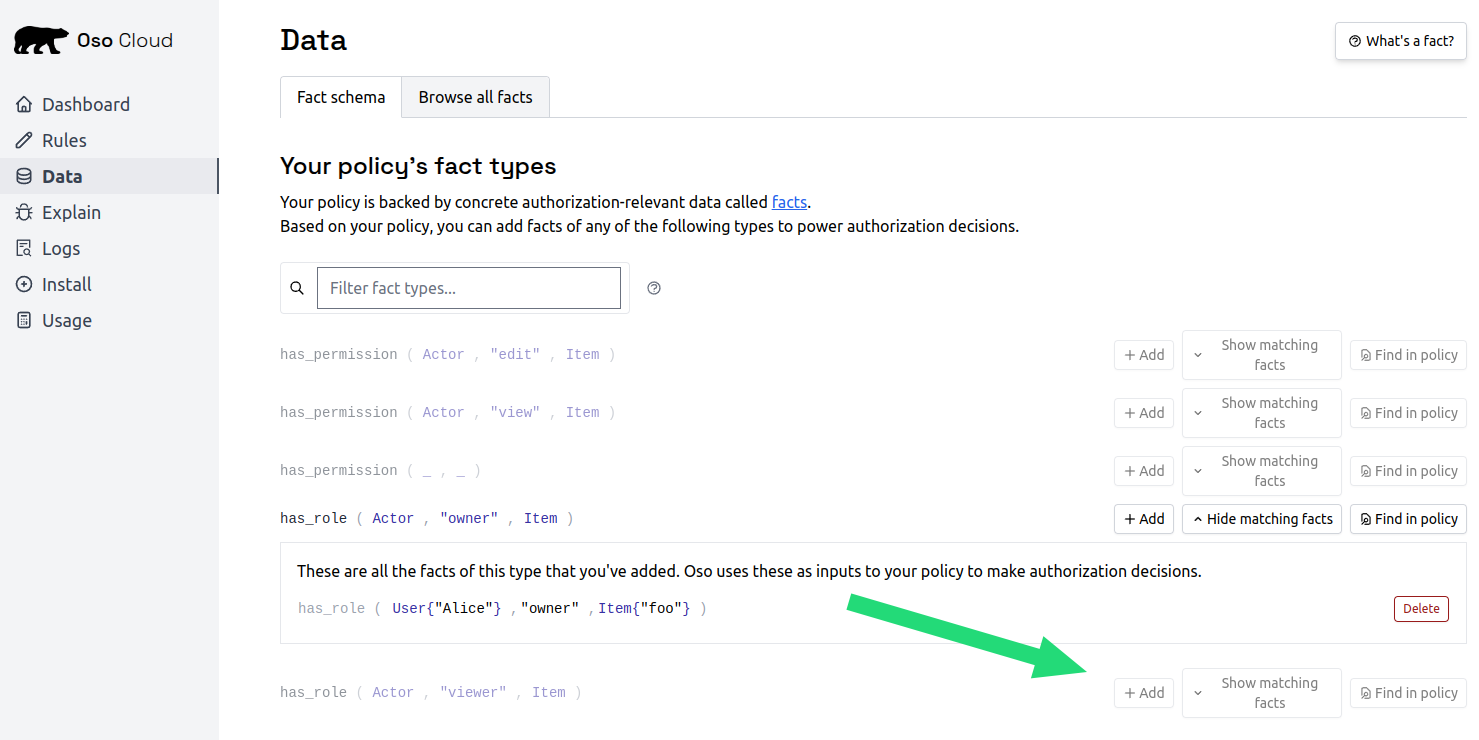
Add Alice as owner
- Open the Data tab
- Click
Addnext tohas_role ( Actor, "owner", Document )
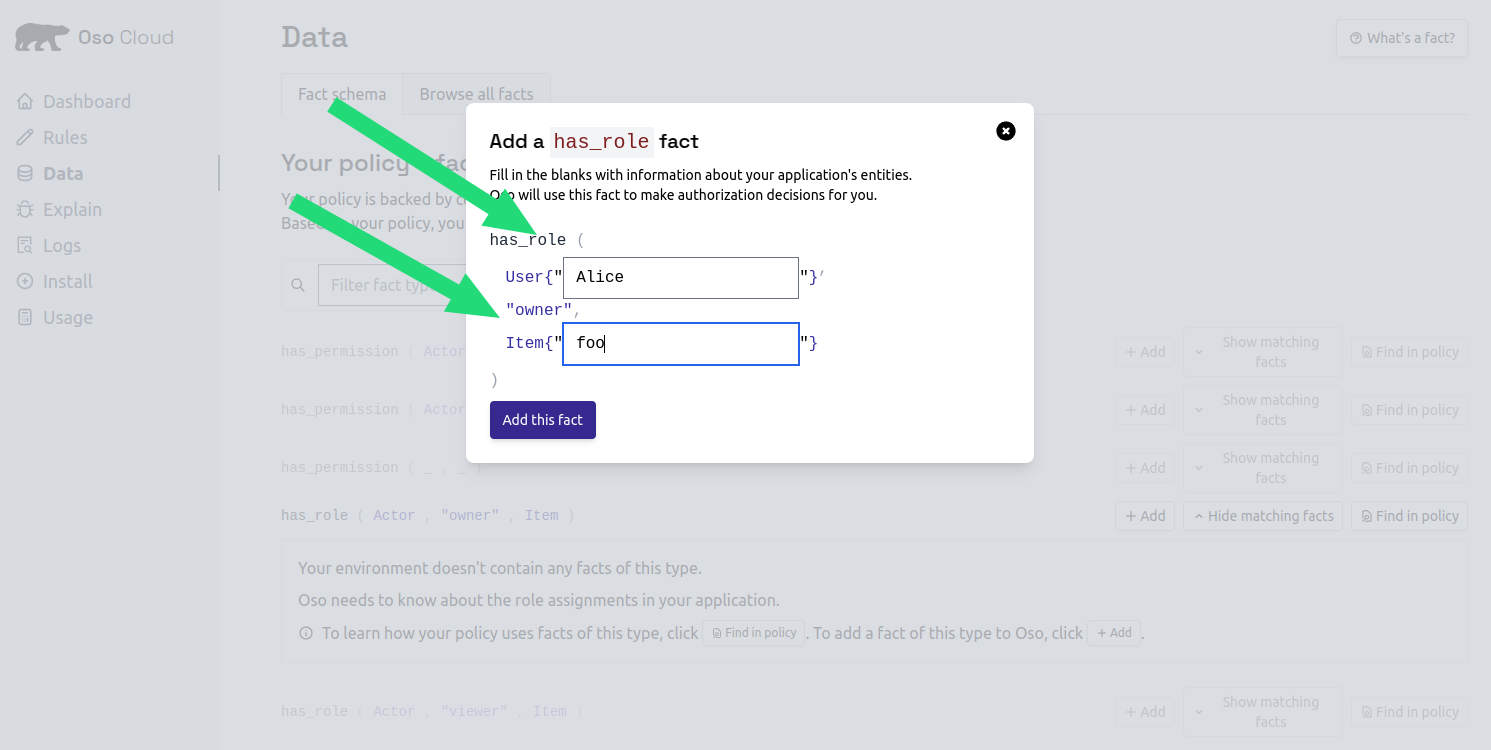
- Enter “alice” as the User ID
- Enter “budget-2024” as the document name
- Click
Add this fact
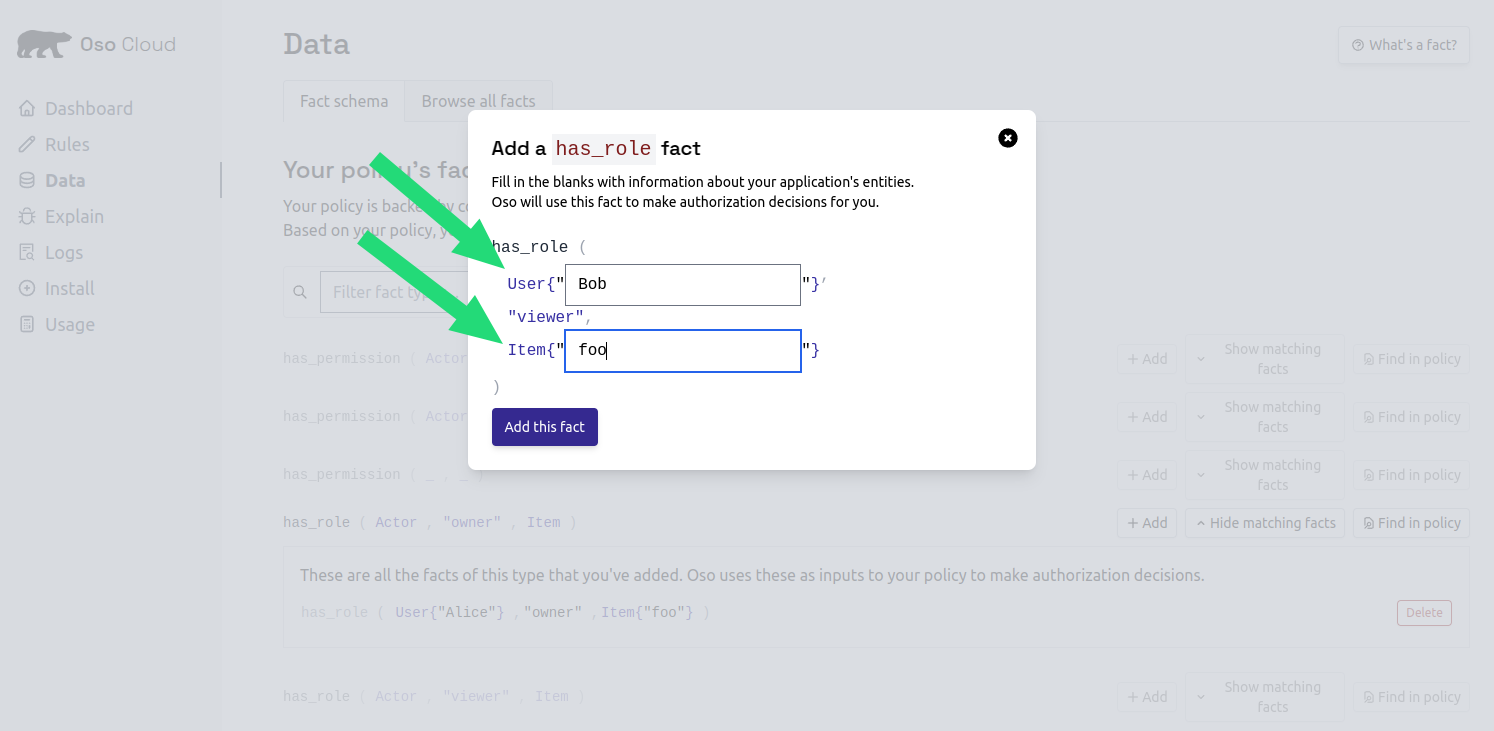
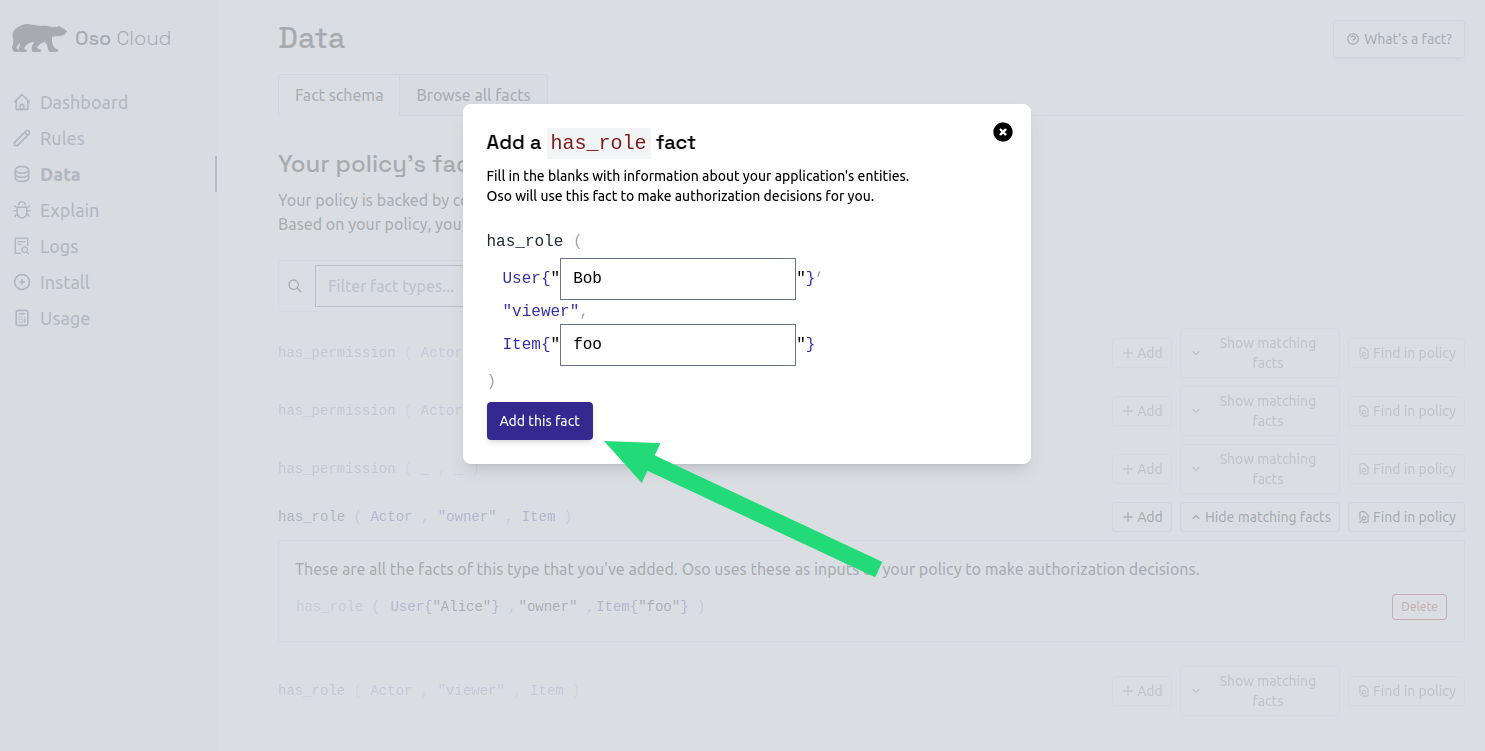
Add Bob as viewer
- Click
Addnext tohas_role ( Actor, "viewer", Document ) - Enter “bob” as the User ID
- Enter “budget-2024” as the document name
- Click
Add this fact
Step 4: test authorization in the console
Test your setup by running authorization decisions in the Oso console. Open the Explain tab to run authorization checks.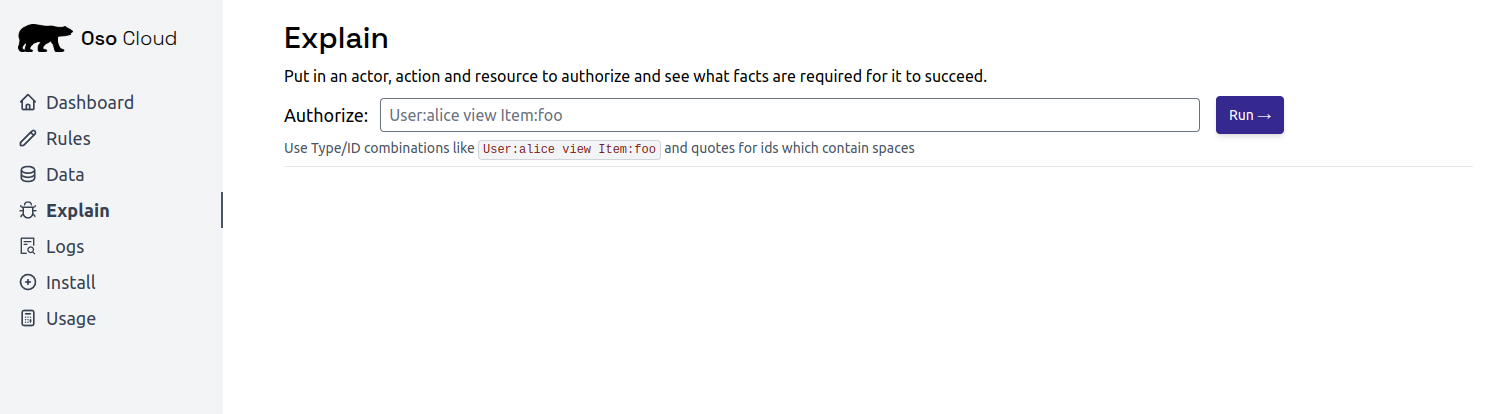
Test Alice’s access
- Enter
User:alice view Document:budget-2024in the Authorize field - Click
Run - Result should be ✅ Allowed (Alice is an owner)
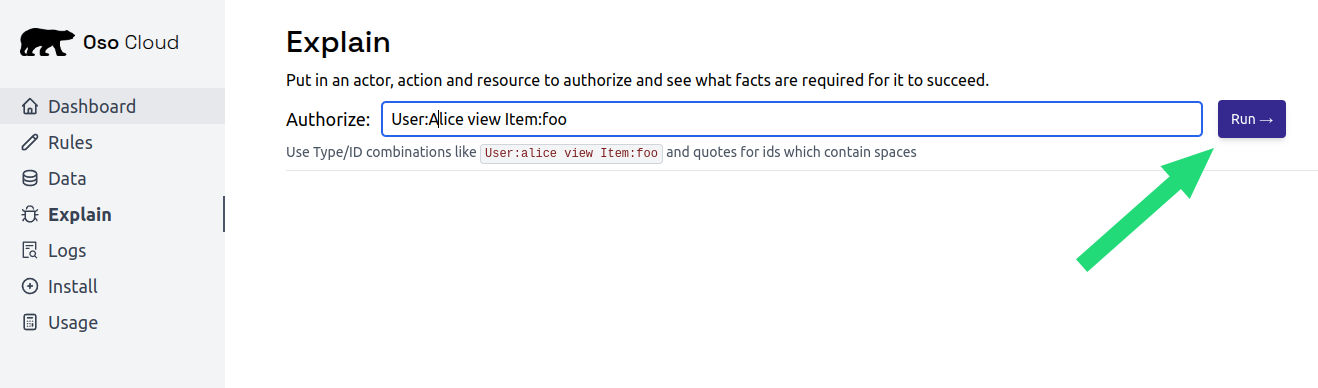
Test Bob’s access
TryUser:bob edit Document:budget-2024.
Result should be ❌ Denied (Bob is only a viewer).
Step 5: install the Oso Cloud CLI
Install the Oso Cloud CLI to start making authorization checks.- MacOS / Linux
- Windows
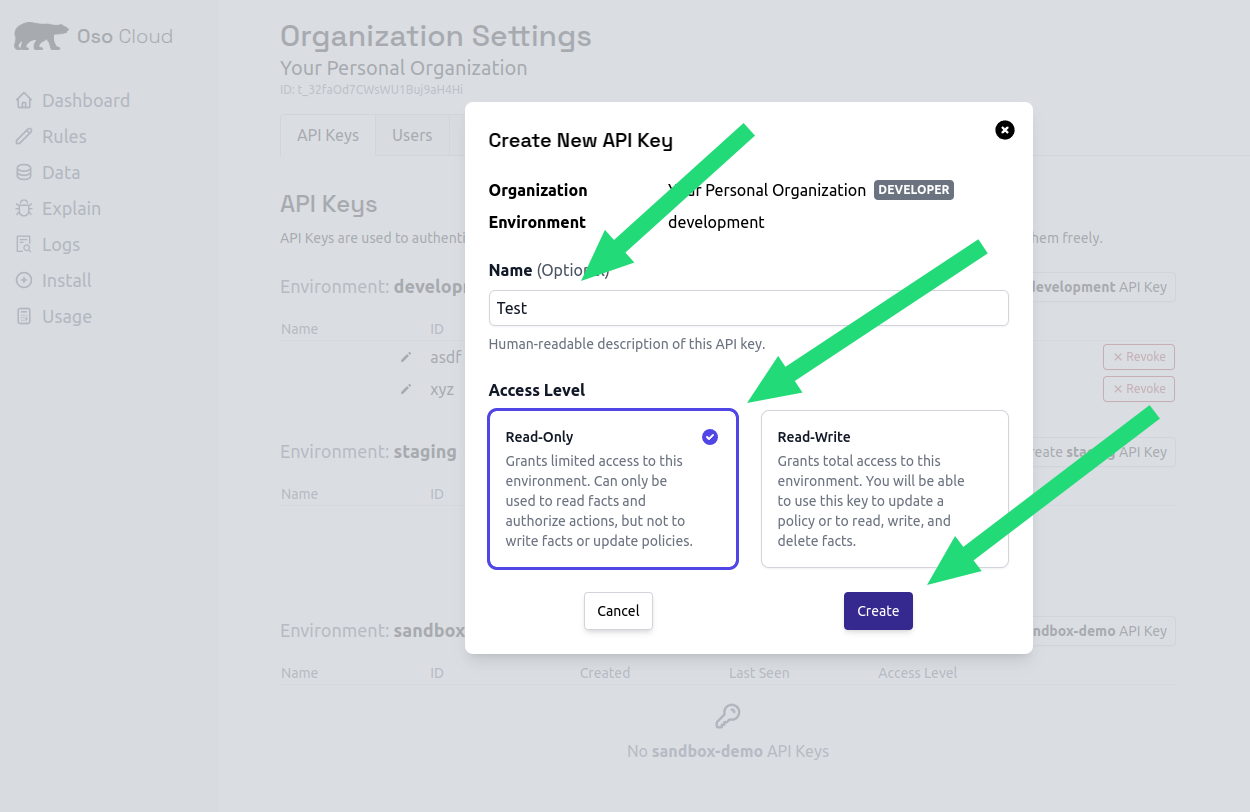
Step 6: get your API key
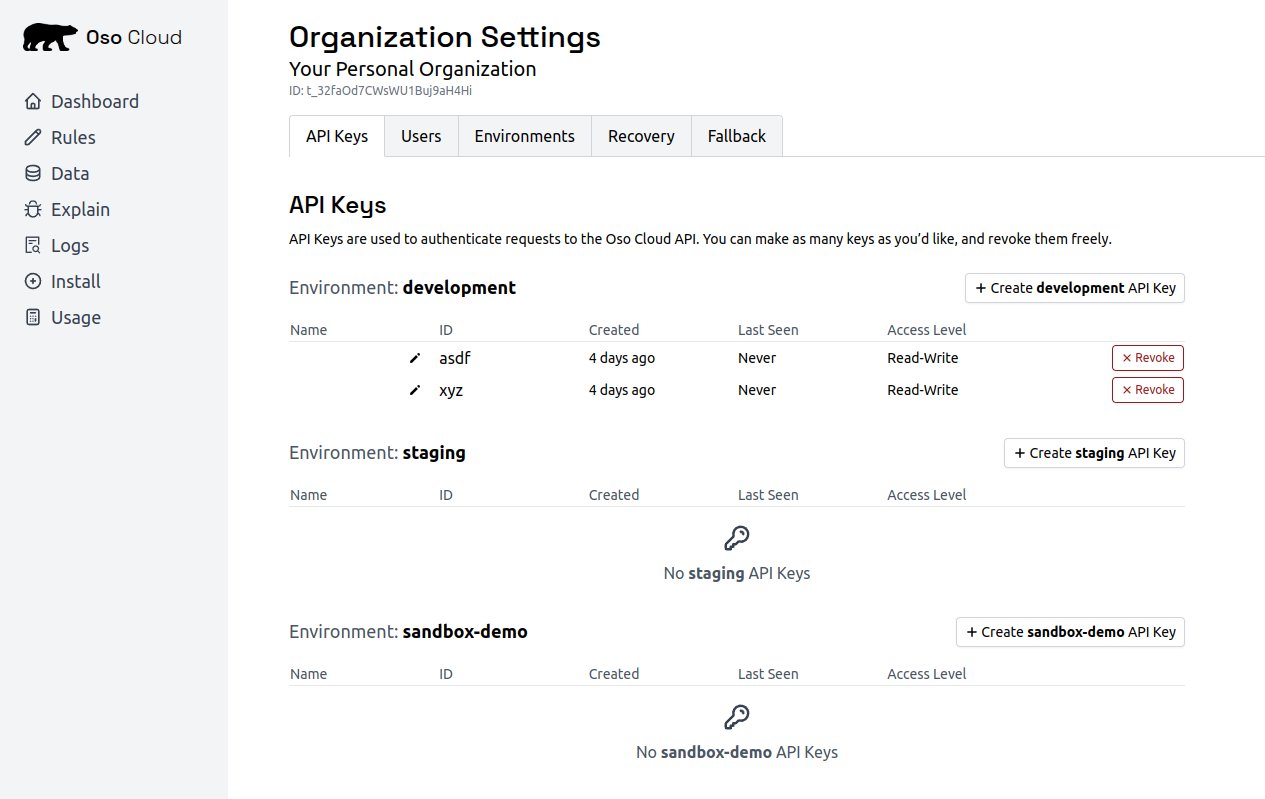
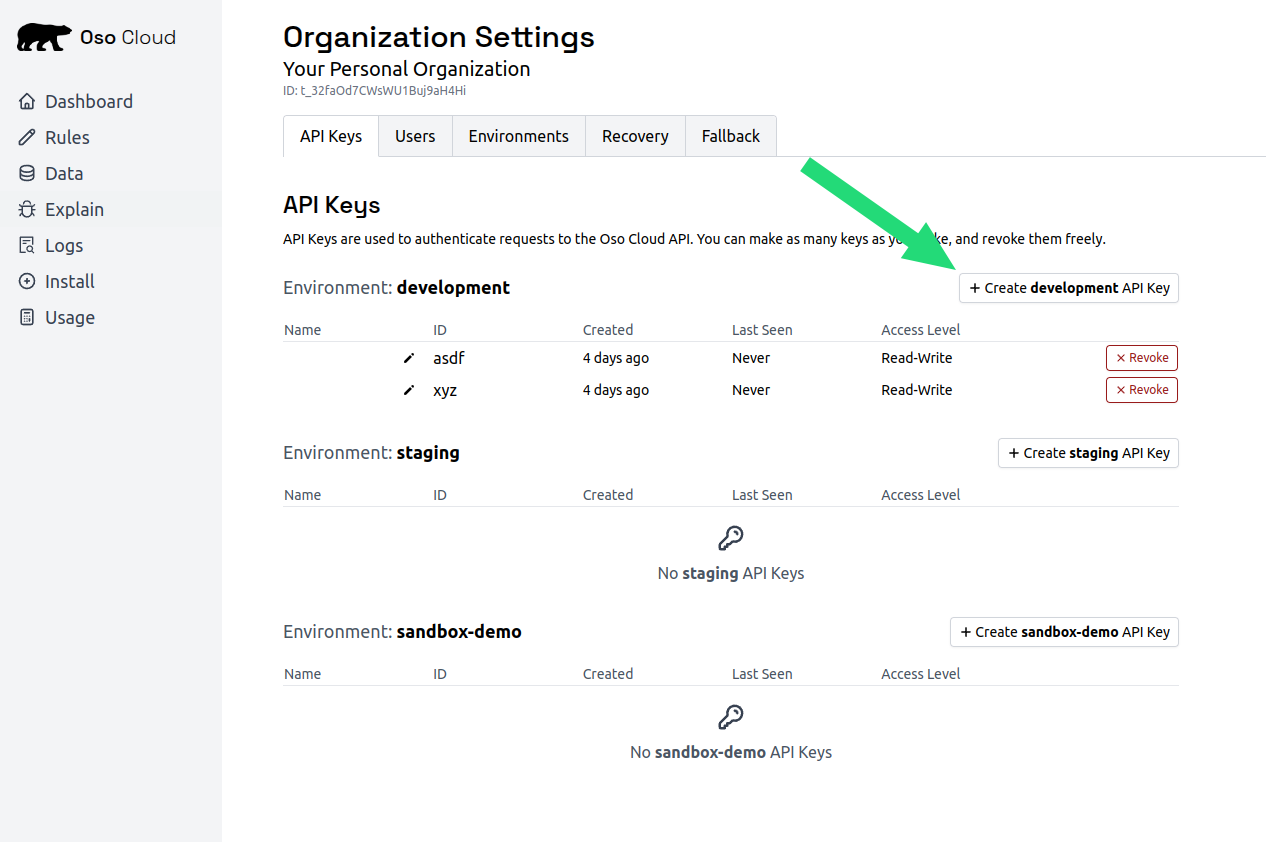
Create an API key to authenticate your application.- Go to API Keys settings
- Click
Create development API key - Name it “Quickstart”
- Select
Read-Onlyfor testing - Click
Createand copy the key
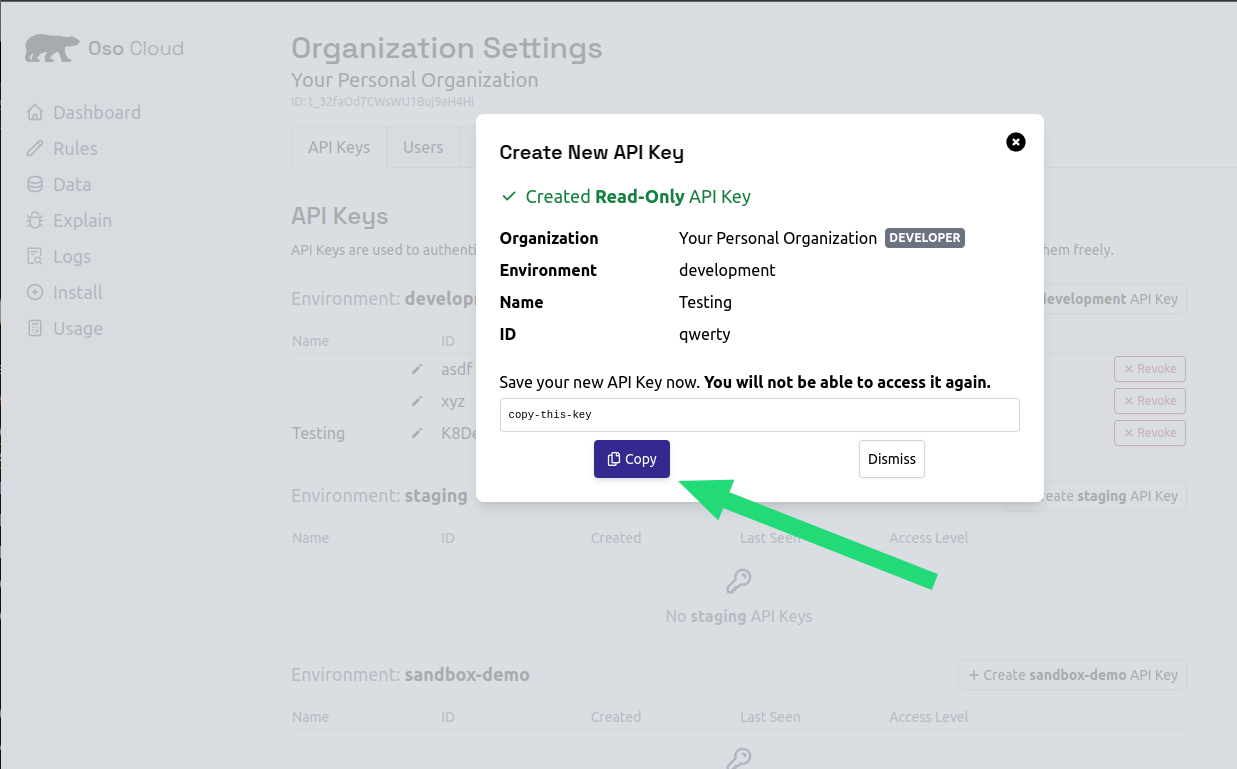
Step 7: set your API key
- MacOS / Linux
- Windows
Make authorization calls
Make authorization decisions in your application code. Test Alice’s access- MacOS / Linux
- Windows
- MacOS / Linux
- Windows
Next steps:
- Model complex policies: learn Polar for advanced rules.
- Local Authorization: filter directly in your DB for performance.
- Sync production facts: keep facts up-to-date with application data.
- Schedule a technical consultation